McAfee and Kaspersky Lab, partners in the project NoMoreRansom, are pleased to announce today the availability of a decryption tool for victims of the Wildfire variant of ransomware. This tool is available following successful collaboration with the Dutch police and the European Cybercrime Centre. This strong public-private partnership has led to the seizure of criminal infrastructure and has resulted in the availability of the decryption tool.
How it Works
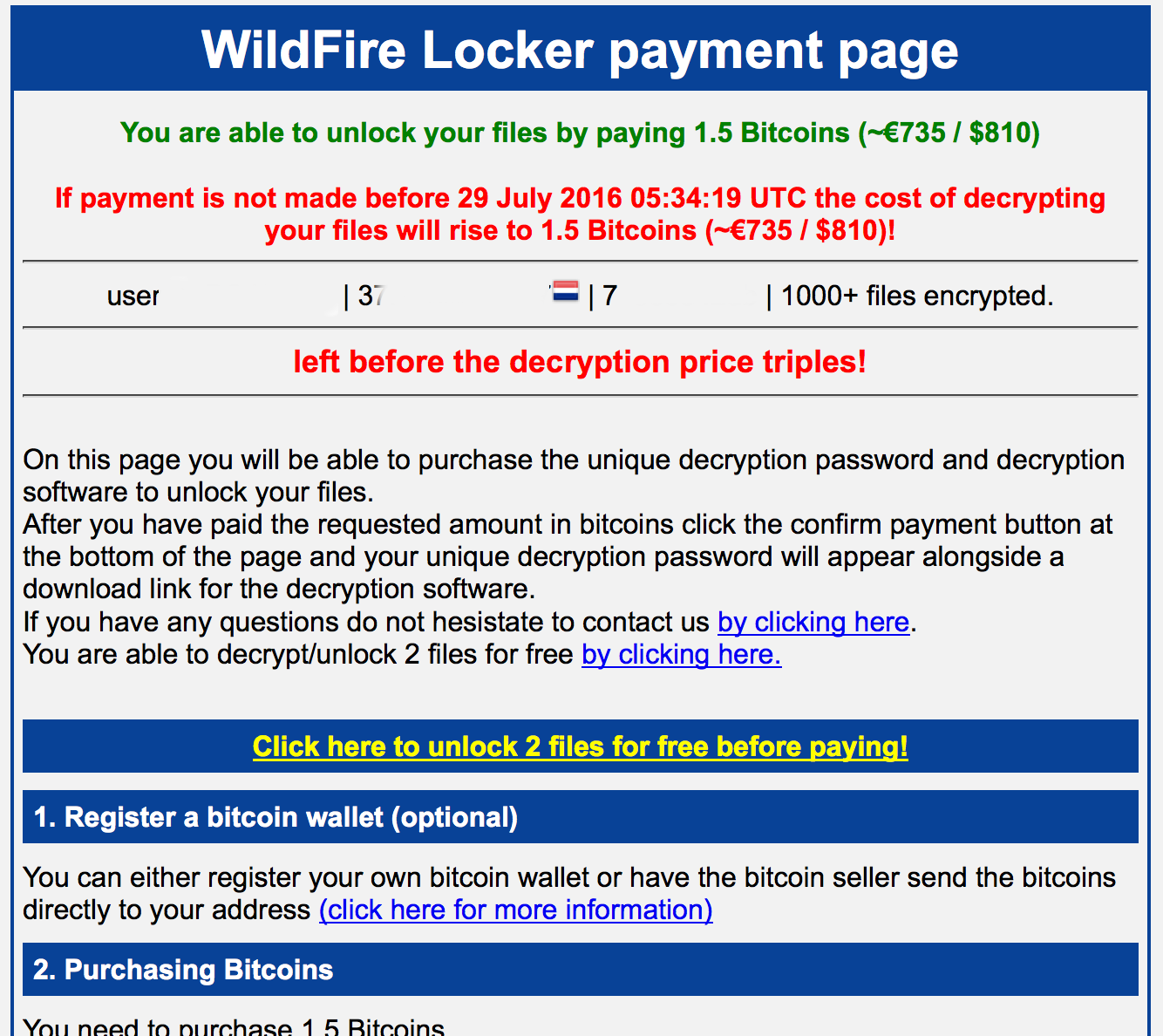
Victims of this variant of ransomware know if they have been infected with Wildfire because they will see the following message:
Ransomware notice.
Most of the victims of Wildfire are in the Netherlands and Belgium. Although this message requests a ransom of 1.5 Btc, reality is that most victims paid between 0.5 and 0.6 Btc. Apparently, the actors accepted in some cases a negotiation.
Wildfire has spread primarily through Dutch spam emails from transport companies, targeted at Dutch speakers. The victims were misled with a notice of a “missed” delivery and instructions for scheduling a new delivery by filling in a “special form” attached with the mail. This form was in fact an obfuscated dropper that infects the victims with the ransomware. The following screenshot is typical of the many spam mails:
Spam email aimed at Dutch speakers.
The domain transportbedrijfpeters.nl, used in the preceding mail, was first seen on May 17 by a P.O. Box company in the United Arab Emirates. May 18 was the date of the spam mail. There is nothing illegal about this, but it raises a lot of suspicion.
The domains used in all the Wildfire spam mails that we researched were registered between the end of May and August this year, the height of the Wildfire campaign. Another remarkable thing about the spam mails is that they contain addresses of real businesses in the Netherlands.
The actors behind Wildfire have clearly put a lot of effort into making their spam mails look credible and very specific. Because of these elements, we would not be surprised if there is a Dutch-speaking group involved.
Once victims are infected, they see the ransom note, as shown above. To make the payment, the victim has to connect to a .RU or .SU domain. These domains act as a proxy to connect the victim to the control server, which was hosted on the Dark web. We believe that the actors did this to avoid the detection of search bots and having the site appear in popular search engines, and to be as stealthy as possible when accessing their services.
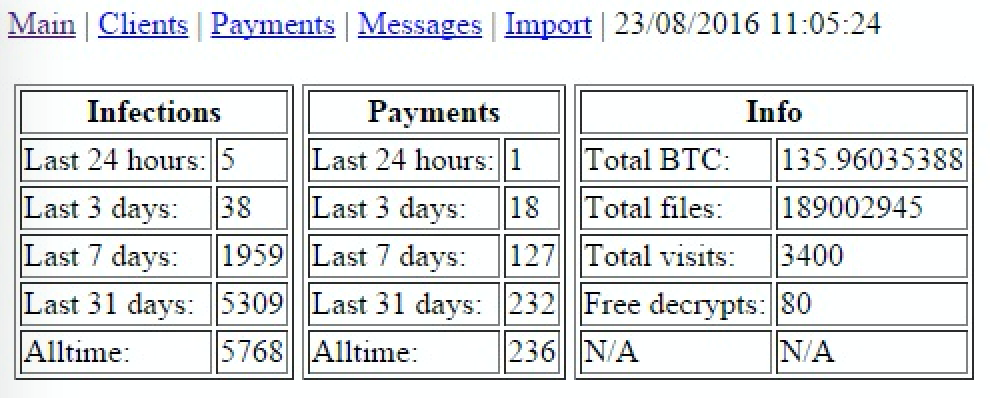
Thanks to our public-private partnership we were able to take a look at Wildfire’s control server panel. The main panel has the following campaign details:
Wildfire campaign overview.
We see from this overview that in the last 31 days the campaign has infected 5,309 systems and earned total revenue of about BTC136 (€70,332). Not a bad “paycheck” for a month.
When we look at the “clients” page, we see details of the amount of encrypted files, their BTC address, files encrypted, and country:
| ID | UID | Country | BTCaddress | BTCamount | Filecount | Paidstatus |
| 1 | a5***** | BE | 1J*************** | 0.6 | 11673 | 0 |
| 2 | aa***** | NL | 1F*************** | 0.5 | 1469031280 | 0 |
| 3 | fd***** | BE | 1H*************** | 0.6 | 68595 | 0 |
| 4 | 08***** | NL | ZC*************** | 0.5 | 1469079732 | 0 |
| 5 | 05**** | NL | GH************** | 0.5 | 1469605876 | 0 |
Overview of victims’ file data.
A table marked as RID with the value “aff_001” might indicate an affiliate program, in which “aff_001” could stand for “Affiliate_001.”
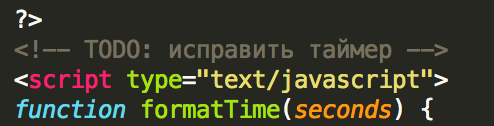
When we take a closer look at the source code of the control server, we see some indicators that make us believe Wildfire is an affiliate-based ransomware-as-a-service (RaaS). The index.php page of the server contains a comment in Russian:
Russian comments on the control server.
The Cyrillic text “исправить таймер” means “fix timer” and refers to the timer function of the ransomware. Another indicator in the config file of the source code is a list of exempted countries. Wildfire will not encrypt victims from certain countries.
Exempted countries in Eastern Europe.
This list is a strong indicator that we are dealing with an Eastern European group. This is not surprising; we have seen this behavior with many other ransomware variants, including CryptoWall.
We would not be surprised if Wildfire is indeed an example of RaaS. The malware shows a very close resemblance to the ransomware variant Zyklon. Another possible giveaway is the difference between the source code found on the control server and the very specific Dutch/Belgium infection vectors found in the spam mails. They are too far apart in language to come from the same actor group. It is worrisome to see large-scale extortion by ransomware made easily available to so many criminals.
Today, however, the victims of Wildfire no longer have to face the difficult choice of either paying criminals or sacrificing their data. The availability of this decryption tool allows victims to reclaim their data without having to pay anyone. The initial tool includes 1,600 keys for Wildfire and more will be added in the near future. The is another result of the NoMoreRansom public-private partnership.